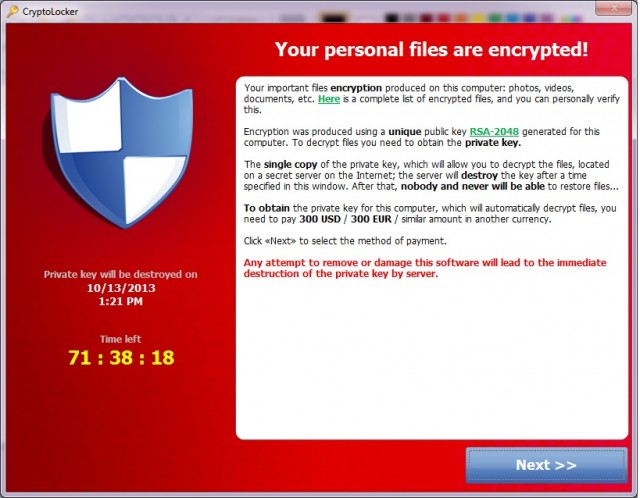
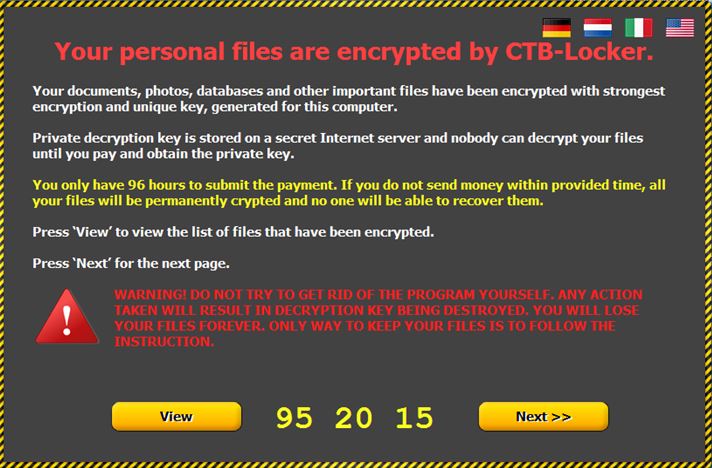
Dance of Shadows
In the ethereal realm where bits and bytes pirouette, hackers, — those modern-day sorcerers — weave spells that transcend the ordinary. Armed with languages like Python, Perl, PHP and arcane JavaScript, they navigate the digital cosmos, probing, and unlocking the secrets that lie veiled in the tapestry of networks. Behold the tools they wield, are instruments of both creation and destruction, from the sacred to the profane.
In the sacred arsenal of ethical hacking tools, the dance begins with Invicti and Fortify Web Inspect, guardians of web sanctums. They scrutinize the labyrinthine codes, seeking vulnerabilities with an ethical gaze. Cain & Abel, an enigma in its own right, whispers into the ears of cryptographic secrets, unraveling the knots of security protocols.
The Network Mapper, Nmap, dons the cloak of a phantom, mapping the unseen terrain of networks, while Nessus, the vigilant sentinel, scans for the faintest echoes of weakness. Nikto, a poetic vigilante, surveys web servers with a discerning eye, unraveling the threads that may lead to digital Pandora's boxes. Kismet and NetStumbler, the ethereal wanderers, roam the airwaves, unraveling the secrets that linger in the currents.
Acunetix and Netsparker, architects of digital fortresses, wield their prowess to shield the sacred domains from malevolent gazes. Intruder, a mischievous sprite, dances on the edges, seeking chinks in armor, while Metasploit, the shape-shifter, crafts exploits that transcend the ordinary.
And in the midnight symphony, Aircrack-Ng emerges, a spectral conductor orchestrating the dissonance of wireless networks, revealing the vulnerabilities that flutter in the unseen air.
In this dance of shadows, we encounter two archetypes - the White Hat and the Black Hat. The White Hat, the virtuous guardian, dons the mantle of ethical hacking, defending the digital realms against nefarious forces. The Black Hat, the elusive trickster, navigates the shadows with malicious intent, seeking to exploit weaknesses for personal gain.
But why, in this dance between light and shadow, do we need these hackers? For in the ever-expanding digital tapestry, vulnerabilities lurk like phantoms in the night. The network, a delicate ecosystem, demands guardians to ensure its integrity. The hacker, a dual-faced Janus, plays the role of both villain and hero, revealing the chasms that may lead to calamity or guiding the way toward fortified horizons.
So, let us not cast judgment upon the hackers, but rather, seek to understand their dance. In their whispers of code and shadowy exploits, lies the echo of our collective vulnerabilities. In the labyrinth of networks, the need for the hacker emerges as an intrinsic melody, urging us to fortify our digital bastions and navigate the cosmic dance between chaos and order.