CYBER ATTACKS
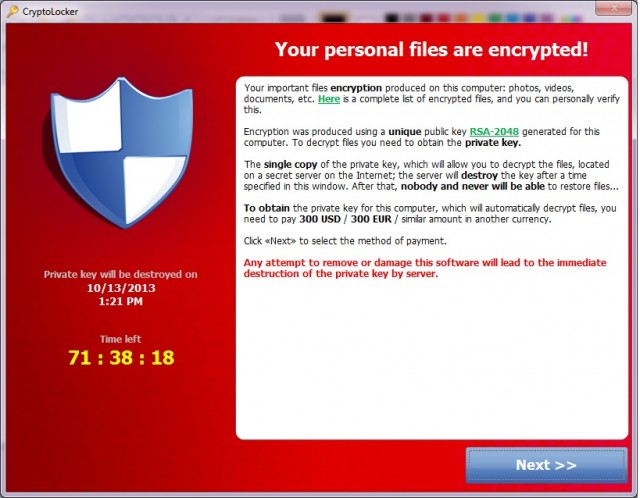
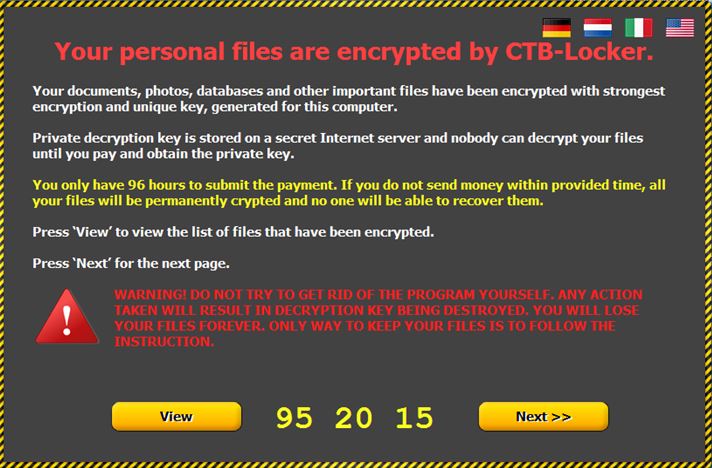
Did you know that Cyber attacks for today exceed 1,523,196 and is about half a million less than yesterday's 2,043,871 cyber attacks. If you don't believe me, you can verify it for yourself here. The malware families that account for about 40 percent of all recorded attacks are from the Worm32.Conflicker, the Virus.Win32.Sality, the Cutwail botnet and the Neutrino Exploit kit. These treats have been religiously turning MS Windows computers into DDoS and spam-spewing botnet drones for at least the past five years. But now, that Cryptowall ransomware version 4 was released, corporate cyber security companies are on a back foot. This is exactly what is portrayed in the Series Mr. Robot when Evil Corp's entire data centre got hacked and encrypted with 256-bit AES encryption. |
| Hacks taking place every the day |
Looking at the daily cyber war far between attacking countries like USA, China, Portugal, Germany, Russia, Sweden, United Arab Emirates, United Kingdom, Netherlands, and Turkey, etc, and target countries like USA India, Chile, Sweden, United Kingdom, Taiwan, Poland, Brazil, Norway, Russia, flinging virus and Trojans at one another is bound to strain relations.
 |
| Hackers are attacking targets across all borders |
Worm32 Conflicker
Banker.Win32.Bancos.K
Trojan.Win32.ZeroAccess.A
Worm.Win32.Brontok.B
Trojan.Win32.Virtu.A
Trojan.Win32.Mwzlesson.A
Virus.Win32.Sality.
Operator.Andromeda.gx
Operator.Cryptowall3.bbe
Operator.Trojan.Win32.Grafter.e.a
Trojan.Win32.Smokeloadr.C