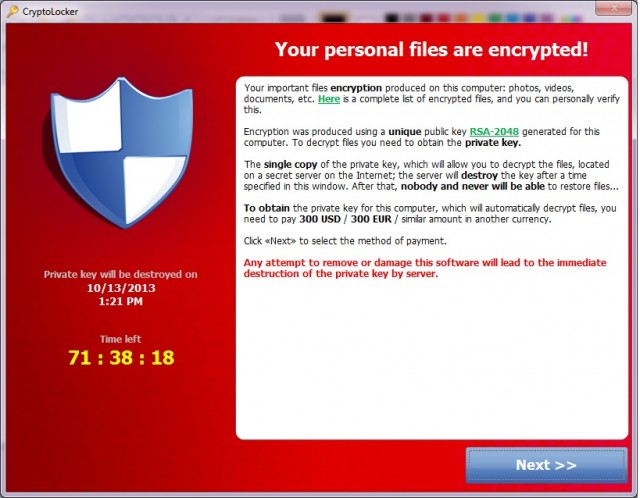
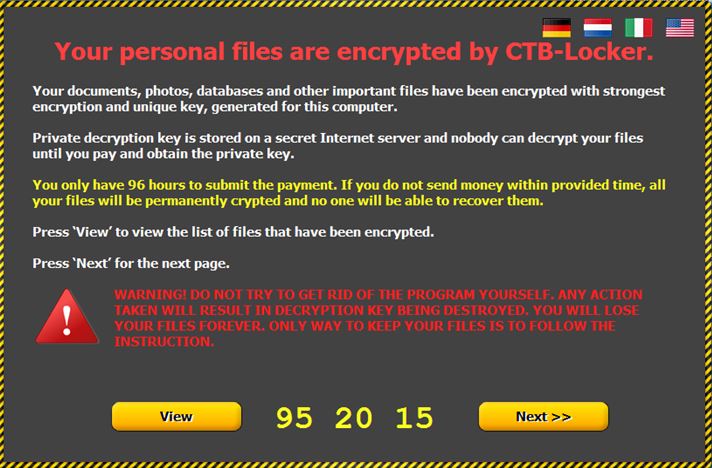
2015 WAS THE YEAR OF RANSOMWARE
Computers and ICT networks are prone to electronic failure but with the expert help of ICT professionals, network up-time can almost be guaranteed to 99.98 percent. However, for the past decade computer and network redundancy and global replication services, ISP's and corporate networks have been under attack from, Heuristic Computer Viruses, Worms, Malware, Spyware, Trojan/backdoors, Adware, Rootkits, Scareware, Keyloggers, and the worst of all Ransomware attacks that appear to be more personal. Not to mention the physical threats by hackers, making the jobs of network security personal more intense and challenging. Costing companies huge additional and unnecessary expenses globally.
It is predicted that Ransomware is going to be the greatest emerging security risk in 2016 and the general consensus is that 2015 has been the year of Ransomware. The purpose behind all intrusion software is to disrupt, create chaos, steal data and extort money. The reasons, avarice, sadism, vindictiveness, arrogance, aggression, envy, anger, bitterness, jealousy, hate, narrow-mindedness and plain unadulterated evil. Can you even imagine a cracker hacking your computer system stealing your personal information as well as take over your computer holding it ransom until you make their specified payment and endure the uncertainty whether or not thy will release you computer once payment is made.
Globally security experts are doing the utmost to reverse engineer Ransonware software in an attempt to put a stop to this thievery.
Surprisingly there are number of them amongst which are TeslaCrypt, Alpha Crypt, CryptoFortress, Chimera , CryptoWall, Ransomware infection, MBR Ransomware (MBR stands for Master Boot Record), CryptoLocker and the worst of all CTB Ransomware (CTB atands for Curve-Tor-Bitcoin). Crowti (aka Cryptowall) and Tescrypt (aka Teslacrypt) are two Ransomware families that cyber gangs and e-criminals used to infect more than half a million Computers running Microsoft Operating System and Microsoft Security Software. In fact the majority of Ransomware is targeted at the Microsoft Windows operating system and is sent as spam and e-mail attachments with the following names.
disgruntled.zip
facto.zip
headband.zip
woodworking.zip
firefly.zip
If the attachment, is unpacked, it unloads a .scr file, which if activated will launch a dropper of the Dalexis class. It will then connects to a series of hard-coded URLs, from which it will download CTB Locker. CTB Locker will change all your file name extensions to .crypt however the various flavours of Ransomware can change it to any of these file name extensions listed below. (NB! This list is not exhaustive)
*.aaa
*.abc
*.cry
*.cpyt
*.crypt
*.crypto
*.darkness
*.ecc
*.enc
*.exx
*.ezz
*.kb15
*.kraken
*.locked
*.nochance
*.obleep
*.vault
*.zzz
One way to combat Ransomware is to keep a snapshots of the files in a secure area of your network that wouldn't be affected by Ransomware if the machine is infected. Alternatively store an offline backup image of your hard drive so that your data can easily be restore. Refrain from downloading or access e-mail attachments from people you don’t know and never click on e-mails links you receive from unknown e-mail addresses. Also make absolutely sure your anti virus / security solution is up to date and able to detect and block CTB Locker, and change your online security protection level by adjusting your web browser security settings.